05 Apr Fake Flash Player Targets Apple Users and WP Engine Clients
Fake Flash Player updates which mask malware have been around since MySpace was hot; Adobe was warning the public not to download the Flash Player from sources outside their download site back in 2008. But despite the publicity, the malware-installing fake downloads persist. Currently, a fake Flash Player scam is targeting visitors and users of the popular WordPress hosting platform WP Engine by taking advantage a common typo of the company URL.
If a webdesigner or WPEngine client accidentally inserts an hyphen (“wp-engine”) into the URL of their development site on WP Engine, they are immediately taken to a page with a pop-up screen warning them that their Flash Player is outdated. The screen apes legitimate warnings that appear when Flash Player truly is outdated. If the user clicks onto the update button, rather than being taken to the official Adobe Flash Player download page, they’ve initiated the installation of the malware onto their computers. To confuse users who suspect something is amiss, the installer also downloads a genuine version of the Flash installer.
The irony is that WPEngine is rated one of the most secure web hosts for WordPress websites, and takes great pride in their robust security settings. (WP Engine customers needn’t be concerned that the webhost has been compromised. The website is never accessed, since the malware redirects from the incorrect URL pulled up from the typo.)
The particular brand of malware installed is appropriately named scareware. The infected computer is overrun with pop-up ads warning of an infection and prompting the user to install malware masquerading as anti-virus software. Going into the Applications folder and deleting the fake Flash download appears to solve the problem. However, once the computer restarts, the pop-up screens appear again, and the fake Flash installer reappears in the downloads folder. Doing a reinstall of the browser prevents subsequent appearances of the pop-up windows, but the malware will reside in the system until an antivirus program such as Malwarebytes Anti-Malware is run.
The Intego Mac Security Blog ran a comprehensive article on fake Flash update scareware last year. According to Graham Cluley of Intego, the scareware manipulates the computer users fear of infected computers to trick them into downloading the fake Flash Player. Johannes Ullrich of SANS Institute reported that the scareware installer took advantage of a valid Apple developer certificate. That permitted the malware to bypass recent OS X defenses which permit only programs downloaded from the official App store or identified developers to be downloaded. (Ullrich pulled together an informative video which shows what happened when he downloaded the fake Flash player.)
Downloading the Flash Player from only the official Adobe website is common sense, and websites which ask users to legitimately update their version of Flash will direct users to this page. The fake Flash Player download continues to be used by scammers. This February, Intego reported that a fake Flash Player is being used to install a sloppy new malware, “MadDownloader.” MacDownloader attempts to steal the users keychain information – passwords, usernames, PINs, etc. – by tricking the user into believing adware software needs to be removed from their system. Although the malware was so poorly designed as to pose little risk, chances are the developers will release an updated version. If a user suspects their version of Flash may be updated, they should check the status via their Systems Preferences or, better yet, permit Adobe to automatically update the program.
As for WP Engine customers: just be sure to not include a hyphen in the domain when you’re typing in the URL for your development platform. If you forget,and that persistent “Flash Player outdated” screen appears, simply quit out of your browser. If. you haven’t downloaded anything, chances are you’re fine. (You can always run your anti-malware software just to be sure.)
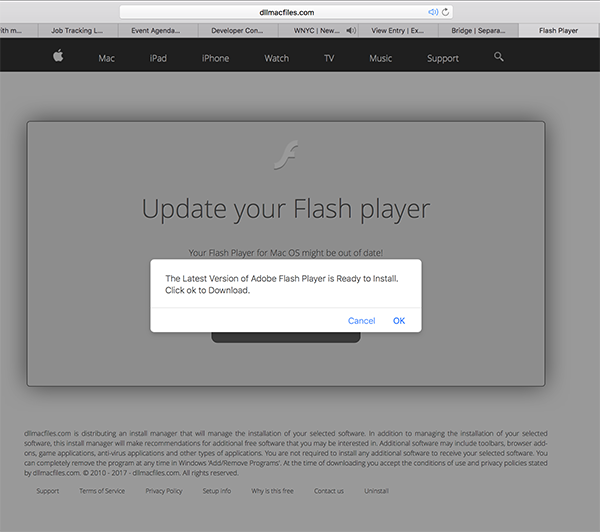
If you accidentally type “wp-engine” into your address bar, you’re taken to a deceptively official-looking Flash update screen. Note the URL is dllmacfiles, not the Adobe Flash download site. The intercept is quite aggressive; a persistent popover window prompts you to install the fake Adobe Flash Player. The fake download screen even includes reassuring verbiage telling you that dllmac is distributing an “install manager.”
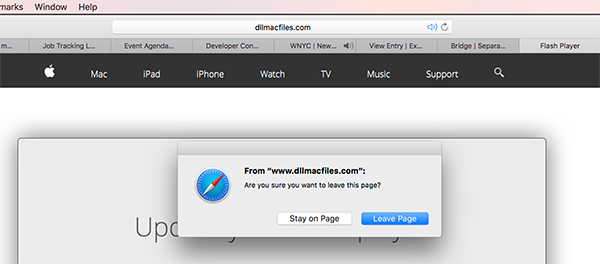
If you click “cancel,” a popover window asks you if you’re sure you want to leave the page. Clicking “Leave Page” averts any problems.